As I walked up to Durant’s I did a double take. The guy leaving looked very familiar but I couldn’t recall where I had seen him before.
I made my way to the back of the restaurant where the Undercover CISO (UC) was holding court at his booth. Chef Ken was buzzing about the UC’s table, offering off-the-menu selections. The UC was dressed more dapper than usual. His Brioni suit was impeccably tailored, with his Rolex occasionally peeking out under his sleeve. His Brunomagli shoes had a shine that would make a West Point cadet proud.
“Looking sharp today, UC,” I said.
“Well, I just had lunch with my CEO. Did you see him?”
That is who I had seen. The UC’s CEO is a darling of Wall Street. Nine consecutive quarters of increasing revenues and the stock had more than doubled over that time.
“So, you are a CISO with ‘a seat at the table’?”
“No, the CEO has a seat at my table,” he retorted.
“Did you beg him for budget?” I wanted to see if I could get a reaction from him.
He didn’t flinch. “I don’t beg for budget. I tell him what I need and he gives it to me.”
“Wow. Care to let me know your secret?”
“Sure,” he began “You never want to live on the left side of the income statement.”
I pondered that for a second. I know the left side of an income statement summarizes a company’s expenses. The right side of the income statement summarizes a company’s revenues.
He continued. “Too often, CISOs ‘live’ in the right side of the income statement. They focus their attention on mitigating losses. Let me be clear up front: losses due to data breaches can be very high. CEOs consistently see cybersecurity as one of their main concerns. Reducing breach expenses is and will continue to be a priority for CISOs. But, the C-suite has more important priorities. Since C-level pay, not to mention C-level jobs, are highly dependent on stock price, executives want steadily increasing revenues.”
Interesting. As Chef Ken delivered our shrimp cocktail I searched my phone for an example. In January 2023 T-Mobile had a significant data breach on the heels of a massive data breach in 2021.
The wireless carrier didn’t indicate what it might do to remedy the situation. It noted that it could be on the hook for “significant expenses” because of the hack, although the company said it doesn’t expect the charges will have a material effect on T-Mobile’s bottom line. [Emphasis mine].
https://www.cnn.com/2023/01/19/tech/tmobile-hack/index.html
The news of the latest data breach comes as the carrier is in the final days of the settlement phase from a 2021 cyberattack that exposed the data of roughly 76.6 million people. T-Mobile agreed to a $500 million settlement in the case in July, with $350 million going to settle customer claims from a class action lawsuit and $150 million going to upgrade its data protection system.
https://www.cnet.com/tech/mobile/another-data-breach-has-hit-t-mobile-impacting-37-million-accounts/
Now $500M is a lot of money even for a company as big as T-Mobile. Despite their costs, security breaches are often ‘one-time hits’ to a company’s expenses. And that is important for CISOs to understand. But don’t security breaches cause extreme damage to a company’s reputation and stock price? Don’t customers leave? Let’s take a look at T-Mobile’s stock price after its latest big breach was reported in January 2023. True, its stock dropped by one percent on the day of the announcement, but it quickly recovered just a few days later. and it has the highest subscriber growth of all wireless carriers.
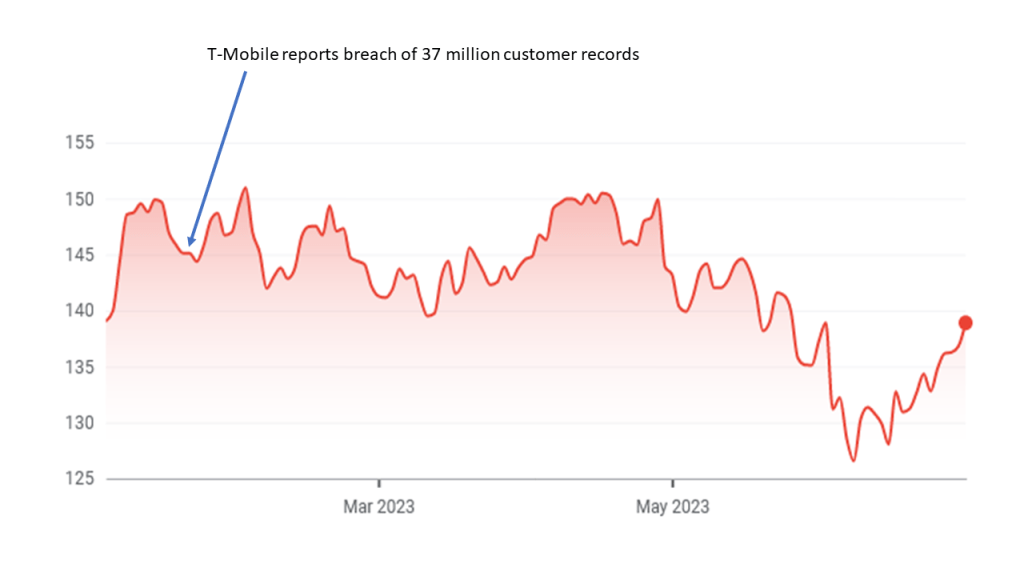
The UC took a sip of his martini and said, “I understand our business like the back of my hand. Most CISOs understand security well enough, but can’t speak to executives in business language. That is my value. How do breaches affect current and future revenues? That is the key question.”
“How do you communicate that with management?”, I asked.
“First, I understand that my job is information security, but my role is risk management. Cyber is just one of dozens of risks that executives must manage. It is not about controls and patches. The hardest thing I do is communicate cyber risk. All risks have likelihoods and impacts, conveyed in dollars. Ninety percent of CISOs can’t quantify cyber risks. Hence, they don’t have a seat at the proverbial table.”
He went on, “If we have a major breach, my job is on the line. If we have a major breach that tanks revenues or the stock price, my CEO’s job is on the line. And the ultimate metric my CEO is rated on is stock price. In fact, only around a quarter of compensation for the typical CEO at an S&P 500 company came from cash salary or bonus. The rest comes from stock and stock options.“
I did a little more research on T-Mobile.
U.S. wireless carrier T-Mobile US (TMUS.O) said on Wednesday it has authorized a shareholder return program of up to $19 billion that will run through December 31, 2024.
The company intends to declare and pay its first dividend of approximately $750 million in Q4 2023, as part of the return program.
It will pay around $3 billion in additional dividends in 2024, with payments occurring each quarter during the year, along with share repurchases.
https://www.reuters.com/business/media-telecom/t-mobile-announces-shareholder-return-program-up-19-bln-2023-09-06/
“Nineteen billion dollars is a ton of money,”
“Yup,” he replied. ”My company is also buying back a ton of stock. Do you now believe that stock price is the paramount concern for executives?”
I pondered that as I took a big bite of my White Chocolate Raspberry Cheesecake. I took a quick look at my watch and told the UC I had to run. I didn’t want to be stuck with the lunch bill. I quickly shook his hand and dashed off.
The UC was always insightful. I summarized in my head the key takeaways.
- Know your company’s business inside and out. How do we make money? Bury your head in your company’s 10-K. Understand all your company’s material risks – not just the cyber risks.
- Understand how cyber risks can affect the right side of the income statement, i.e., revenues, not just costs.
- Understand that your job is to manage information security, but to express your security posture to management in terms of risk. Speak the language of the business. Express cyber threats quantitatively in dollars.
On my way out and while thanking Chef Ken for another excellent meal, I heard a shriek from the dining room. Oh dear. The UC had spilled his 2019 Robert Craig Cabernet on his Brioni suit and white Canali shirt.

